LDAP
Lightweight Directory Access Protocol (LDAP) is a directory access prototcol which can act as a gateway or a directory service itself.
An entry is what we call a record in the LDAP server, it is the same as a record in the traditional database. A LDAP entry is made up of many attributes. Attributes are divided into name/value pairs, these attributes are the same as fields in a traditional database. An attribute will have only one name but it can have more then one value, the value can be text or binary.
Each entry is uniquely identified by it's distinguished name (DN). The DN is made up of components each of which is called a relative distinguished name (RDN). The components from the RDN are taken from the attributes in the entry.
Object classes determine what attributes are available for an entry. They are the same as tables in a traditional database. They differ from tables in a database because they are extensible. Basically this means to can declare a new object class that extends from an earlier one.
Each server will have a schema. The schema is the blue print of the server and it specifies all the object classes and attributes that are available to be searched and stored in a LDAP server.
The directory service is accessed like a tree and is reffered to as a Directory Information tree (DIT). The directory server itself is called a Directory Service Agent (DSA).
The Data Format
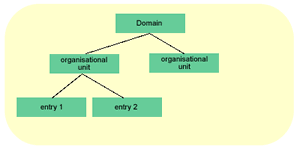
The data in an LDAP server is organised in a hierarchical/relational format. It is hierarchical becuase every entry in the server, apart from root is below another entry, it is relational because you can group entries together. The top level is called the domain and the branches are in the form of organisational units, normally departments in an company. These organisational units can then be sub-divided into sub-divisions. Each entry that is neither a domain or organisational unit is called a leaf.
Below is a basic LDAP hierarachy:

LDAP Installation
There are a number of steps to install, configure and test a secure LDAP server
1. Obtain hardware (server and client)
2. Install solaris 9 (server and Solaris 8 (client)
3. Patch both servers
4. Obtain sun one directory server 5.2 software
5. Install directory server packages (32 or 64 bit, recommended to use 64bit for high volumes)
6. run idsktune (checks patches and recommendations)
6a. optionally install the directory server SDK from Sun
7. configure the directory server ("directoryserver configure -nodisplay" command)
8. configure admin server ("mpsadmserver configure -nodisplay" command)
9. create object class, containers, ACI's and client profiles ("idsconfig" command)
10. setup the VLV indexes (commands are display after idsconfig)
10a. check that nis objects exist ("ldapsearch -b cn=schema objectclass=* | grep nisDomainObject" command)
11. Enable TLS/SSL via the admin gui
12. configure the clients ("ldapclient init ...." command) alter nsswitch.conf and starts the ldap_cachemgr daemon
12a. check client ldap files in /var/ldap (ldap_client_file and ldap_credential_file)
13. configure pam.conf file on the client
14. testing the client ("ldaplist" command)